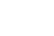Windows 7 continues using a registry similar to that of windows XP. In the same way, with frequent installing or removing Programs, the registry will keep bloating, which will not only be a waste of hard disk space, but will affect system boot speed and the efficiency of the registry access in programs running. So, the first thing to maintain the registry is cleaning up it. I will introduce two ways.
Method 1:Clean up registry manually, which contains 5 steps
Method 2 Clean up registry by a professional registry cleaner
Method 1: Clean up registry manually
Step 1: Rebuild registry
The registry file use a way similar to database records that when delete a key at a certain time, just removed the logo, but not the actual information. The information is still retained in the registry file; of course, the space occupied by the key will not be released. After a period of time, the registry will be significant growth in volume. However, rebuilding the registry is a good method to reduce the volume of registry.
First, click START menu, run the regedit program, export the whole registry from the Registry menu and then save it as new.reg. Then go into the state of pure DOS by using use DOS boot disk, and rebuild the registry through the command “C: Windows regedit / c new.reg”. The parameter “/ c” express that re-generate the entire registry from the specified file in the later. The reconstruction of the registry files are often much smaller than the original ones, so you can optimize the registry.
Step 2: Delete useless registry files
There are many useless programs in Windows registry. You can find and delete those sub keys which have been deleted under primary keys “HKET_LOCAL_MACHINESoftware” and “HKET_CURRENT_USERSoftware. And you can also delete unnecessary key values. For example, you can delete languages and input methods under the primary key “HKET_LOCAL_MACHINESystemCurrentControlSetControlKeyboardlayouts”.
Step 3: Remove invalid files association
The contents related with files association the registry file are stored in the key “HKEY_CLASSES_ROOT”, whose “a-z” section is used to define the file type and “A-Z” section is used to record the application that open the files. Generally speaking, when the second section of the keys opens a suspicious key, if there is no content in sub key, then this key is empty.
Step 4: Remove rudimental key of uninstalled software
Much software will leave some useless information in the registry files after uninstallation. They are generally stored in the keys “HLEY_LOCAL_MACHINE Software” and “HKEY_CURRENT_USERS _T (Software AppEvents EventsLabels . Default”. You can find and completely remove the residual information of the uninstalled software.
Step 5: Delete redundant DLL files
A number of useless DLL file information or VxD file information can be found through registry, after delete which the system can improve the operation efficiency . The specific approach is to open key “KHEY_LOCAL_MACHINE Software Microsoft CurrentVersion SharedDLLS” in the registry, the project under the sub-key contains the number of applications that shared this DLL files. If a DLL file corresponding to the number zero, it means that it is no longer useful to system, you can delete it without worry.
Method 2:Clean up registry by a professional registry cleaner
The method 1 seems too complicated to many people who are unfamiliar with windows registry. They may easily remove important keys. The best choice I think is to use a professional registry cleaner.
To choose a registry cleaner, the most important thing is that it should be a safe and stable one to operating system. It won’t delete useful files from our computers and then strongly impact computer performance. It should have a powerful function of fixing registry errors and optimizing registry. Personally, I like Wondershare registry optimizer which has integrated functions like clean and optimize registry, IE manager, Stat up manager, uninstall manager and back up tools. It is very easy to use, just click START button, your registry will be clean up soon. What’s more, you can use its additional functions to optimize registry and system. For example, Wondershare registry optimizer has a fixing function, by which you can fix registry errors.
It is very easy to use, and can be divided into 4 parts: registry cleaner, privacy cleaner, shortcuts cleaner and restore.
I will introduce the operation of the main cleaning function.
registry cleaner is used to scan and clean your cluttered registry. Simply click the scan button to run a comprehensive or customized scanning through Windows registry.

After scanning your Registry, there will be a brief report for it. Click Continue button to clean the unnecessary information.
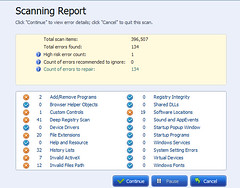
Click continue button, you will see all errors with different risk ranks and you can choose to repair them or not.

Click repair button, you will see the same dialogue window like the below one. You have easily and quickly fix all your registry errors.
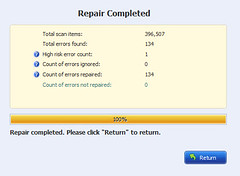
The registry optimizer can also optimize system, clean privacy, remove useless shortcuts, and make backup for your computer. If you want to know more information about it, just have a try.
Source by Samaire Cage